One of the things I’ve been looking to expand in our Melbourne vCAC demo environment is the AWS side of things. Sure, provisioning a workload is great but it doesn’t really show you the full extent of what we can do. The most immediate need was to show that you could actually access the workload post provisioning.
[two_thirds]After configuring an Entitlement to allow SSH access to our Linux AMI, all I could see was the following. RDP to a Linux host? Um…[/two_thirds]
[one_third_last]
[/one_third_last]
[bra_divider height=’40’]
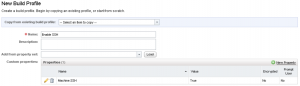
[two_thirds]I vaguely remembered that in 5.2 there was a Custom Property that had to be applied to a Linux Blueprint to allow for SSH, and sure enough when I investigated in the vCAC Custom Property Reference I found that the Machine.SSH property is still alive and kicking. So, first things first let’s create a Build Profile with this property in it – this is the more scalable way to assign a Custom Property (or multiple Custom Properties) to Blueprints. Head to Infrastructure > Blueprints > Build Profiles and enter the information as found in the screenshot to the right. [/two_thirds][one_third_last]
[/one_third_last]
[bra_divider height=’40’]
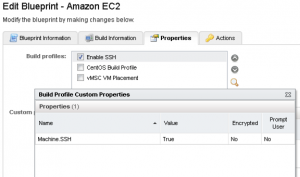
[two_thirds]Now let’s enable it in the Blueprint. Simply tick the box, and if you want to be doubly sure as to what properties you’ve just attached to the Blueprint, click the little magnifying glass and it will display them. Please be aware that these custom properties are applied at the Building Machine phase, so any previously provisioned workloads from the Blueprint you modify will not inherit the setting.[/two_thirds][one_third_last]
[/one_third_last]
[bra_divider height=’40’]
[two_thirds]Having done that and provisioned my AMI, I now get the option to SSH to my EC2 Instance – it looks like we’re on the right track.
The next dilemma is that when I actually attempt that, Firefox tells me that there is no program associated with the protocol (SSH). Now, while we could associate that with Putty, I’d like to maintain the look and feel of VMRC and launch it in a web page. A quick search revealed that (for Firefox at least) I could download the FireSSH plugin to do that.[/two_thirds]
[one_third_last]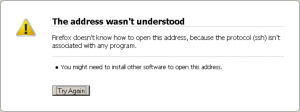 [/one_third_last]
[/one_third_last]
[bra_divider height=’40’]
[two_thirds]Having installed that plugin, restarted Firefox and logged back into vCAC, I get the following prompt. Of course, in order to authenticate I need the Private Key – but how on earth do I get that without having to login to the EC2 console? Surely I should be able to manage all of this through vCAC right? [/two_thirds][one_third_last]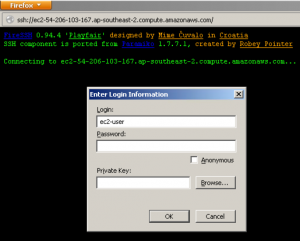 [/one_third_last]
[/one_third_last]
[bra_divider height=’40’]
[two_thirds]In fact yes you should, and yes you can. You’ll need to go manipulate the appropriate Entitlement to include the “Export Certificate” action. [/two_thirds][one_third_last]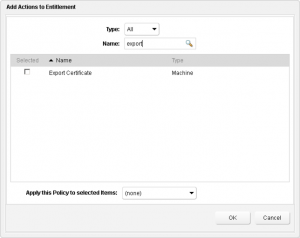 [/one_third_last]
[/one_third_last]
[bra_divider height=’40’]
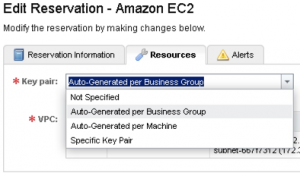
[two_thirds]As you may expect, this now gives us an Action that allows us to export the Private Key for use during authentication. It’s worth mentioning at this point that the keypair utilised for this is defined in the Reservation when you select from the options in the screenshot to the right.[/two_thirds][one_third_last]
[two_thirds]Finally, we attempt the connection again enter the login details and browse to the Private Key and – voila – an SSH connection is established.[/two_thirds][one_third_last]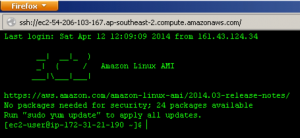 [/one_third_last]
[/one_third_last]